Cloud and security are two terms that have long been considered difficult to “unite” in the world of technology. This perception still exists today—whenever cloud computing is discussed, it is often immediately associated with security issues. Some people even assume that cloud computing is inherently not secure. So, is cloud computing actually safe?
One of the issues often raised regarding cloud computing is accessibility. Data in cloud environments is perceived as being more easily accessible by “anyone,” not just the company itself. If attackers or black-hat hackers target cloud computing environments, they may potentially gain access to more data or resources compared to attacking traditional IT environments.
Cloud Computing: Get to Know More
Understanding cloud computing and security is essential before concluding that cloud computing is “unsafe.” A proper understanding of cloud computing and security also helps individuals and organizations determine the most appropriate cloud solutions from a security perspective.
Security controls in cloud computing are generally not very different from those in typical IT environments. However, due to the nature of cloud services, operational models, and cloud technologies, the risks involved differ from those found in traditional IT environments.
In general, the level of security—whether in cloud computing or traditional IT—can be assessed by examining how security controls are implemented. Are security controls applied across one or multiple layers, including facilities (physical security), systems (system security), data (data security), applications (application security), and networks (network security)? In addition, security controls should also be applied to management and processes, such as segregation of duties across functional roles.
In cloud computing, from my perspective, there is an additional layer—virtualization security, which can also be categorized under system security.
Key Points to Highlight
Cloud computing integrates multiple infrastructure elements. As a result, ensuring consistent security levels across different entities presents a significant challenge. In traditional IT environments, administrators typically have full control over the entire infrastructure. This is not always the case in cloud computing environments, where control is often distributed and shared—adding complexity to ensuring consistent security.
For organizations that are new to cloud computing, understanding the following points is crucial to avoid misconceptions and confusion.
Perception to Minimize Confusion
-
Cloud computing providers are often described based on how their services are delivered. Public and private clouds are sometimes equated with external and internal environments; however, this is not always accurate and depends on the specific context.
-
The way cloud computing services are used is often described in relation to management responsibility and the security perimeter. It is important to clearly understand the boundaries of security responsibility.
From a security perspective, cloud computing should not be viewed solely in terms of “external” and “internal,” which relate to the physical location of assets, resources, and information. It is equally important to consider who is consuming these resources, who is responsible for their governance, security, and compliance with policies and standards.
This does not mean that on-premise or traditional IT environments—physical assets, resources, and information—do not influence security risk.
What Needs to Be Underlined
Security risk depends on several factors, including:
-
The type of assets, resources, and information being managed
-
Who manages them and how they are managed
-
How controls are implemented and integrated
-
Compliance with applicable policies and standards
One frequently overlooked yet critical security entry point is the application layer. Many on-premise and cloud computing environments invest heavily in security protection but fail to adequately secure their applications.
Attackers and black-hat hackers think differently. They often do not care whether the environment is traditional IT or cloud-based—their objective is to obtain as much information as possible to achieve a full takeover of the IT environment.
Conclusion
Cloud computing cannot be considered “unsafe.” Fundamentally, both traditional IT/on-premise environments and cloud computing environments can be secure—provided that all security aspects are properly and comprehensively implemented.
Indonesian Cloud Computing: How We Secure
Established in 2011, Indonesian Cloud is an independent cloud service provider (CSP) specializing in managed IT services based on the principles of on-demand, dynamic, and pay-per-use.
Indonesian Cloud strives to be Indonesia’s most trusted, reliable, and secure local cloud service provider. This is achieved by implementing best-in-class, independently certified technologies; working with top-tier suppliers; employing highly skilled professionals; and deploying cloud platforms in the most secure data centers in Indonesia.
Indonesian Cloud services are part of a comprehensive IT solutions portfolio, including infrastructure, business solutions, and consulting.
Our Security Model
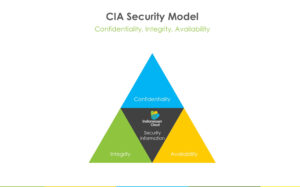
To ensure comprehensive security across all aspects of our cloud services, we implement the CIA Security Model—Confidentiality, Integrity, and Availability. By applying the CIA model, we aim to provide the highest possible level of security.
CIA Security Model
Confidentiality
Only authorized individuals, processes, or systems are granted access to information. All data is protected against unauthorized disclosure (e.g., hacking or cyberattacks).
Integrity
Information and systems are protected from unauthorized or accidental modification (e.g., hacking or attacks).
-
Data Integrity: Ensures information remains accurate, consistent, and trustworthy
-
System Integrity: Ensures systems function as intended
Availability
Information and systems are ensured to be operational and accessible at all times.
The implementation of the CIA Security Model is further supported by five additional principles to ensure a highly secure Indonesian Cloud computing environment:
-
Accountability
-
Authentication
-
Authorization
-
Accounting
-
Assurance
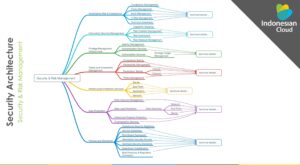
To support the CIA Security Model, Indonesian Cloud implements a comprehensive Security Architecture that ensures all aspects and processes align with CIA principles.
Closing Statement
It is important to understand that security is dynamic—there is no such thing as 100% guaranteed security. However, we continuously strive to implement the strongest possible security measures to ensure a robust and reliable security posture.
This concludes our explanation. If you would like to read more technology-related articles or obtain further information about Indonesian Cloud products, please visit Indonesiancloud.com and our VPS website cloudhostingaja.com. See you in our next article.
Herwono W. Wijaya
Security & Virtualization Consultant @Indonesian Cloud