Backup is not enough for ransomware. Backups can restore data after an incident. However, ransomware creates a bigger problem than “files are back.” Services can stop. Operations can stall. Also, recovery can take time. So, you need a layered ransomware resilience plan, not a single control.
Backup Is Not Enough for Ransomware Because Attacks Have Changed
Modern ransomware is rarely instant. Attackers often enter through a small gap. Then they stay quietly in the network. Next, they study systems, including backups. Finally, they pick the right moment to encrypt or delete data. As a result, when the attack becomes visible, the impact is often widespread.
Backups Recover Data. They Do Not Prevent Attacks.
Backups help you recover data. However, they do not detect suspicious behavior. They also do not stop ransomware spread. And they do not keep services running during the incident. Therefore, backups help after the attack, not during the attack.
The Real Limits of Backups During Ransomware
Here are common reasons why backup is not enough for ransomware:
1) Backups Can Be Targeted
If backups are connected to the main network, ransomware may reach them. In some cases, backups get encrypted. In other cases, they get deleted on purpose. Then the last recovery path is gone.
2) Restore Is Not Always Fast
Restore is not instant, especially at scale. Apps, databases, and dependencies take time. Meanwhile, services stay down. So, financial and reputation damage can keep growing, even if data returns later.
3) Backups Do Not Fix the Root Cause
Backups bring back data. However, they do not close the security gap used by attackers. Without root-cause remediation, the same incident can happen again.
4) You Can Still Lose Recent Data
Backups run on a schedule. So, there is always a gap. Data created after the last backup may be lost during restore. For daily operations, this can be a major issue.
Ransomware Impact Is Not Only About Data
Ransomware also affects service availability, customer trust, regulatory compliance, and team readiness. In many cases, the biggest pressure is restoring services fast, not just restoring files.
A Layered Approach to Ransomware Resilience
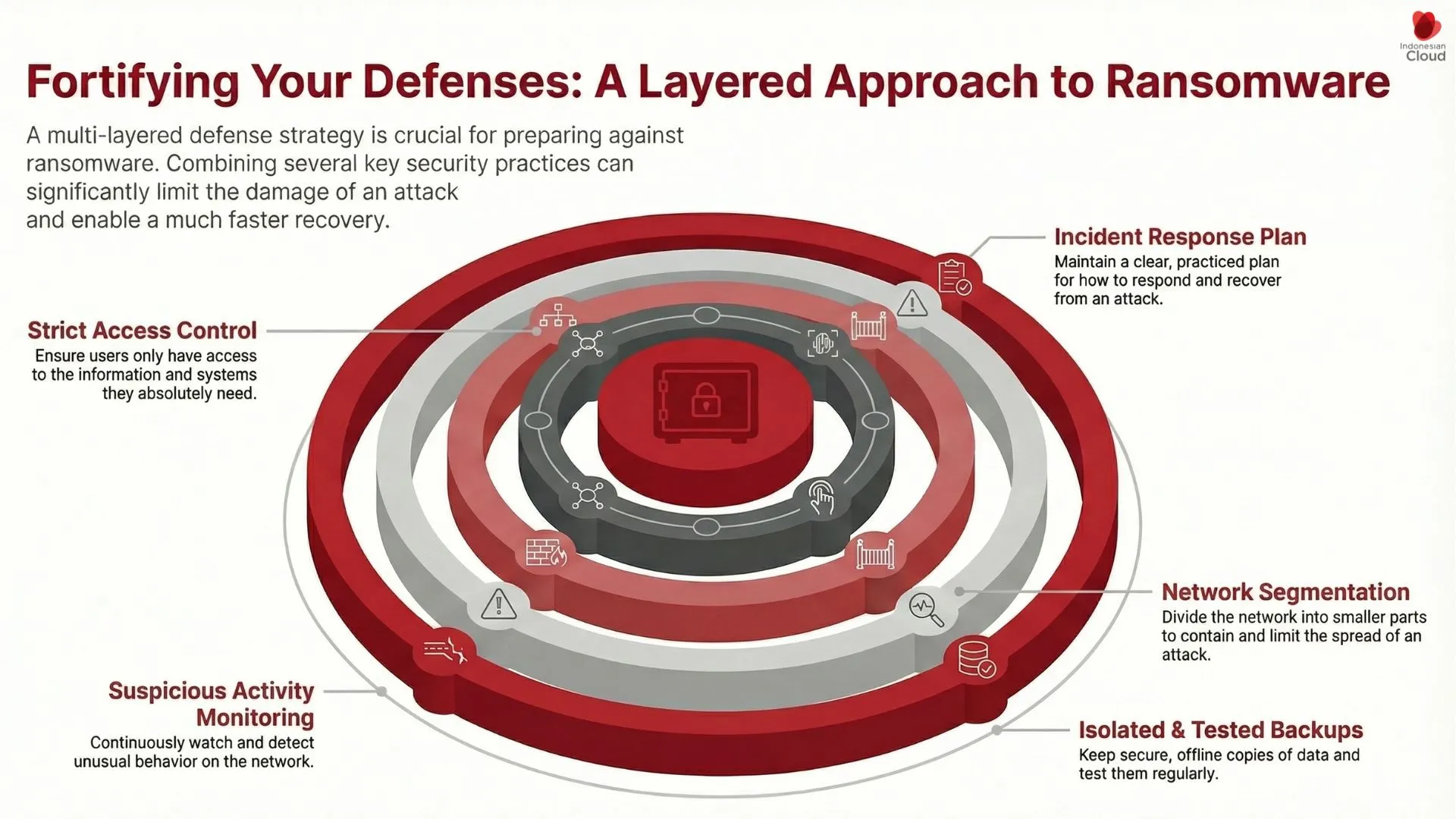
To improve cyber resilience, treat backups as one layer. Then add more layers:
Use Isolated and Tested Backups
Keep backups isolated. Test restores on a schedule. This proves recovery works under pressure.
Monitor for Suspicious Activity
Add monitoring to detect abnormal behavior early. The earlier you catch it, the smaller the blast radius.
Segment the Network
Network segmentation helps limit lateral movement. As a result, ransomware spreads less.
Tighten Access Control
Use least privilege. Limit who can access critical systems and backup controls. This reduces the chance of a full takeover.
Prepare an Incident Response and Recovery Plan
Build a clear playbook. Define roles, steps, and recovery priorities. Otherwise, teams lose time during a crisis.
Conclusion
Backup is not enough for ransomware because attackers target more than files. They can disrupt services, damage trust, and slow recovery. Therefore, a resilient plan must be layered. Use isolated and tested backups, strict access control, suspicious activity monitoring, network segmentation, and a clear incident response and recovery playbook.
If you want a practical ransomware resilience plan, Indonesian Cloud can help you assess gaps, improve backup isolation, and design DR/BCDR to speed up service recovery. Contact Indonesian Cloud to plan the right recovery targets for your critical systems.

